Database as a Data Source for Authentication
A database table is used as data source for the access data.
- Name of the database table - The table name can be chosen freely, usually USER.
Required fields - The following data fields are obligatory:
Required fields Data type Explanation USERNAME String Saves the username as a string. PASSWORD byte[] Saves the password as a byte array, usually encrypted. Data structure generated by RapidClipse
Entities
Attribute Data type Explanation username String Saves the username as a string. password byte[] Saves the password as a byte array, usually encrypted. Data Access
UserDAO
RoleDAO
ResourceDAO
- Additional data fields - If required, the USER table can also include other data fields, since they are not relevant for authentication. Frequently used information about a user include e-mail, status (enabled or disabled), image, time zone, last session, IP address, URL for a log file, etc.
- Dealing with an existing USER table - If you already have a table for managing users in your database, make sure that there is an appropriate entity with corresponding DAO in your Project Management in Entities or Data Access. If not, you can generate the missing entity and DAO with the Create JPA entities from table import function. Different table and field names are no problem because the mapping is performed later.
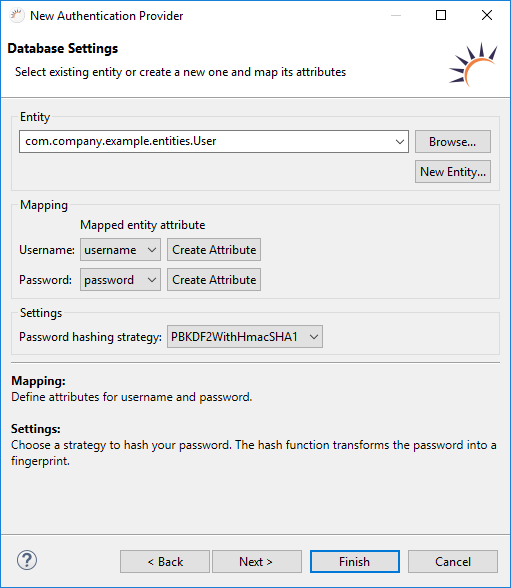
- User Entity already exists - Select your existing User entity.
No User Entity available yet - Click New Entity... to create a new User entity, including the UserDAO DAO. - Select the attribute for the username under Mapping > Username.
- Select the attribute for the password under Mapping > Password.
- Select the encryption algorithm for the password under Settings > Password hashing strategy, e.g. PBKDF2WithHmacSHA1.
- Click Finish.
Go to authorize
Create database table USER - A corresponding table has to be created for the new User entity in the USER database. For this, RapidClipse offers an export feature.
Options:
Mapping
Username - Selection of the attribute for the user name.
Password - Selection of the attribute for the password.
- Password hashing strategy
MD5 - The message digest algorithm is a hash function that creates a 128-bit hash value from a password. However, this is no longer considered secure.
// Example RapidClipse cb9086f37a2e96bd5e4507f869888261
SHA1 - The Secure Hash Algorithm 1 is a hash function that creates a 160-bit hash value from a password.
// Example RapidClipse 64d88c018c7ced7e248e42b48593bd82c5e80ef2
SHA2 - The Secure Hash Algorithm 2 is the currently recommended standard for SHA that creates a 224-, 256-, 384- or 512-bit hash value from a password.
// Example RapidClipse eafa795b8ffea05d1c8a7d5142bd4dd50fea3dd447f3585071e5c8b2ef525cef
PBKDF2WithHmacSHA1 - Combination of PBKDF2, HMAC and SHA1 which creates a 160-bit hash value. PBKDF2 (Password-Based Key Derivation Function 2) is a standardized function for deriving a key from a password and is often used for password-based authentication. HMAC (Keyed-Hash Message Authentication Code) is a Message Authentication Code (MAC), the construction of which is based on a cryptographic hash function. SHA1 - is a hash function that creates a password from a 160-bit hash value.
// Example RapidClipse eafa795b8ffea05d1c8a7d5142bd4dd50fea3dd447f3585071e5c8b2ef525cef
Result:
Project Management > Entities - The User.java entity class is created with the attribute username of the type string and the attribute password of the type byte[] or by selecting an existing entity.
Entity Attribute Data type Explanation User username String Saves the username as a string. password byte[] Saves the password, usually encoded as a byte array. Project Management > Data Access - The UserDAO.java DAO class is generated. When selecting existing entities no new DAO is generated.
Project Management > Business Objects - The ExampleAuthenticationProvider.java class is generated.
package com.company.example.business; import com.company.example.entities.User; import com.xdev.security.authentication.Authenticator; import com.xdev.security.authentication.AuthenticatorProvider; import com.xdev.security.authentication.CredentialsUsernamePassword; import com.xdev.security.authentication.jpa.JPAAuthenticator; import com.xdev.security.authentication.jpa.HashStrategy.PBKDF2WithHmacSHA1; public class ExampleAuthenticationProvider implements AuthenticatorProvider<CredentialsUsernamePassword, CredentialsUsernamePassword> { private static ExampleAuthenticationProvider INSTANCE; public static ExampleAuthenticationProvider getInstance() { if (INSTANCE == null) { INSTANCE = new ExampleAuthenticationProvider(); } return INSTANCE; } private JPAAuthenticator authenticator; private ExampleAuthenticationProvider() { } @Override public Authenticator<CredentialsUsernamePassword, CredentialsUsernamePassword> provideAuthenticator() { if (this.authenticator == null) { this.authenticator = new JPAAuthenticator(User.class); this.authenticator.setHashStrategy(new PBKDF2WithHmacSHA1()); } return this.authenticator; } }
Example:
Save encrypted password
String password = this.passwordField.getValue(); byte[] encryptedPassword = new HashStrategy.SHA2().hashPassword(pw.getBytes()); User user = new User(); user.setPassword(encryptedPassword); try { new UserDAO().save(user); } catch (Exception e) { // TODO: handle exception }
Note:
- Save password and edit - Forms are commonly used for both storing and editing data. However, for storing and editing passwords, you need to create different forms. When saving, the password is entered into the database table encrypted so that you will always receive an encrypted password during reading access. Re-saving would encrypt the already encrypted password again and thus it would be invalid.
- Enter passwords in the database manually
XDEV Software Corp. - One Embarcadero Center, San Francisco, CA 94111, US
Copyright © 2015. XDEV Software Corp. All rights reserved.